The end of passwords? 🗝
A new passwordless standard is being adopted
Year 2049 is the weekly newsletter that discusses the impactful innovations, discoveries, and research shaping our future.
If this was forwarded to you, subscribe for free to get a new story in your inbox every Friday.
Comic
Story: The end of passwords?
“Open Sesame!”

The One Thousand and One Nights folk tales (aka the Arabian Nights) are a big part of my culture and childhood. The tale that stuck with me the most is Ali Baba and the Forty Thieves.
Ali Baba, a poor woodcutter, notices a group of forty thieves entering a cave where they’ve hidden their stolen treasures. But this cave is unlike any other. It’s magically sealed. You can only open it by saying “open sesame”.
While Ali Baba manages to safely get in and out of the cave with a bag of gold coins, his brother Kasim isn’t as lucky. Filled with greed, Kasim learns about the cave and takes a donkey with him to steal as much gold as possible. Once he’s ready to leave the cave with his bags of gold, he forgets the password and gets stuck. When the thieves return and find him there, they kill him. This isn’t how the tale ends but you can read the summarized version here.
Of course, my 10-year-old self used “opensesame” as the password to my first-ever email address.
Passwords are sacred and personal. They protect the digital caves where we store our valuable information, documents, photos, and secrets. But hiding so much behind a few characters can make us feel uneasy and paranoid about getting hacked. Is there a better way?
The problems with passwords and 2FA

Like Ali Baba’s tale has shown us, passwords are an inherently weak form of protection. Digital passwords are even more vulnerable:
Poor security: Passwords are hashed and stored on a company’s servers, which can be hacked. Even if we create unique and different passwords, data breaches can make us vulnerable. Yahoo, Marriott, eBay, and LinkedIn have all experienced massive data breaches in the past 10 years.
Poor usability: It’s difficult to come up with unique and strong passwords for all of our different accounts and remember each one of them. And if we reuse passwords, exposing one of them makes all of our accounts vulnerable.
In recent years, two-factor authentication (2FA) has added a new layer of security to protect our accounts and it has been very effective according to Google:
“an SMS code sent to a recovery phone number helped block 100% of automated bots, 96% of bulk phishing attacks, and 76% of targeted attacks.
On-device prompts, a more secure replacement for SMS, helped prevent 100% of automated bots, 99% of bulk phishing attacks and 90% of targeted attacks.”
But like a predator forced to adapt to a new environment, hackers have evolved and developed more sophisticated schemes.
Phishing scams have become harder to identify because it’s so easy to make a fake-but-legitimate-looking website that tricks you into entering your password and 2FA code.
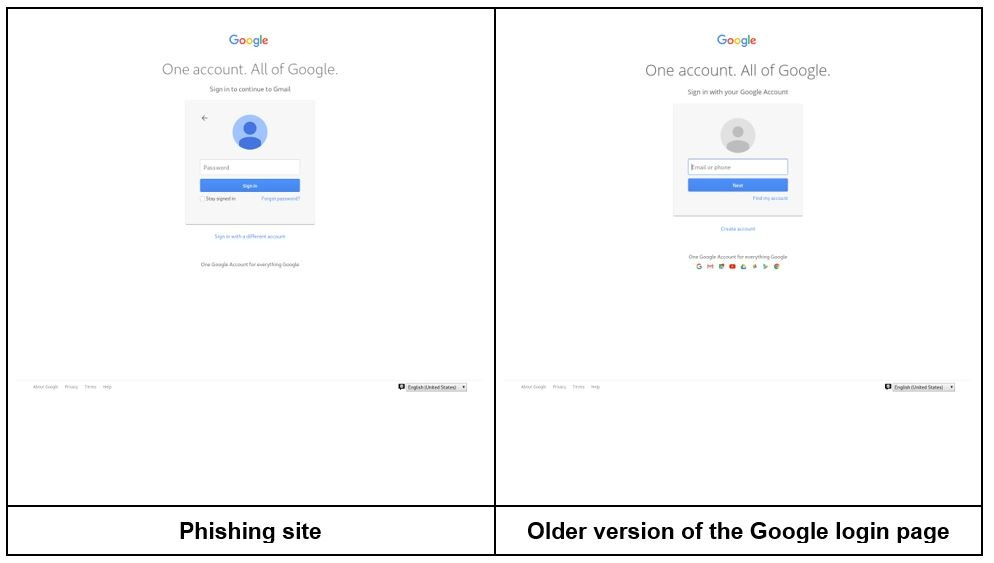
🥷 Safety Tip: If you want to find out if your email or phone number was part of a data breach, you can check it on this website. I checked mine while writing the story and found that my email has been in 9 data breaches.
FIDO Alliance and the new passwordless standard
Now, a new passwordless standard is being adopted by the biggest gatekeepers of the digital world.
To protect their reputations and users, companies have teamed up to form an open industry association called FIDO Alliance. Its 250+ members include:
Big Tech: Apple, Amazon, Google, Meta, Microsoft, Twitter
Governments: Australia, UK, US, Germany, Thailand, South Korea, Taiwan
Payment Providers: AMEX, VISA, Mastercard, PayPal
Password Managers: 1Password, Dashlane
Since it launched in 2013, FIDO Alliance’s mission has been to develop “authentication standards to help reduce the world’s over-reliance on passwords”.
Last week, Apple, Google, and Microsoft announced that they would adopt the Passkey standard developed by FIDO Alliance and the World Wide Web Consortium (W3C). More specifically, two new capabilities will be introduced:
Multi-device FIDO credentials: This will allow us to access our “passkeys” on multiple devices, even if we lose our phone or get a new device, without having to re-enroll each account.
Using our phone as a roaming authenticator: Using Bluetooth to communicate between our phone and the device from which we’re trying to log in to verify that it’s actually us. Bluetooth can only be accessed by physical proximity, which prevents us from getting hacked by a remote third party.
How passwordless logins will work
The user experience around FIDO credentials would be very similar to that of using a password manager that helps the user sign in, but the level of security is better than even traditional two-factor authentication—all without requiring any additional steps or devices during authentication. Typically, all a user would have to do on a new device to sign into a relying party is to pass the built-in biometric challenge on the device from which they’re trying to sign in.
– FIDO Alliance in its latest white paper
Here’s what the overall user experience will be like:
Registering a new account:
You create a new account for an app/website and choose FIDO as your authentication method.
An authentication request is sent to your phone to confirm your identity.
Once you authenticate, FIDO creates a private key and public key unique to your account:
The private key is stored on your device.
The public key is stored by the online service (it’s worthless without having access to the private key).
Logging into an account:
You enter your username to log into the app/website.
An authentication request is sent to your phone, which must be nearby.
To approve the login, you would have to authenticate with your PIN or a fingerprint/face biometric scan.
Do they store my biometric data? Companies don’t store your fingerprint or face biometric data. It’s usually encrypted and stored on your device, without being uploaded to a server or backed up to the cloud. For example, Apple stores your fingerprint/face biometric token in something called a Secure Enclave which is a separate hardware area in the phone.
“It can’t be accessed by the OS on your device or by any applications running on it. It's never stored on Apple servers, it's never backed up to iCloud or anywhere else, and it can't be used to match against other fingerprint databases.”
– Apple
A question for you
Which authentication method do you prefer?
👁 Passwordless login with biometrics
I’ll share the results in next week’s newsletter.
Deep dive
If you enjoyed today’s story, I’ve compiled some additional links to satisfy your curiosity:
Ali Baba and the Forty Thieves summary (Interesting Literature)
Check if your email address or phone number was part of a data breach (Have I Been Pwned?)
How hackers can bypass 2FA with a new kind of phishing scam (Maureen Data Systems)
How FIDO standards have made it possible to be free of phishing (YouTube/Microsoft Security)
Image: The black hole at the centre of the Milky Way
The Event Horizon Telescope collaboration captured an image of a black hole at the centre of the Milky Way, called Sagittarius A*. It’s only the second-ever image of a black hole and the team behind this had to combine the images of eight different telescopes (🤯).
“They collected nearly 4 petabytes (4,000 terabytes) of data, which was too much to be sent over the Internet and had to be carried by aeroplane on hard disks.”
– Nature
Read about the achievement here.
Previous episodes you might enjoy
📱 Matter, the new standard connecting all IoT devices – highly recommended if you enjoyed today’s story
🚗 Guide: The 6 Levels of Driving Automation
🔋 Bidirectional Charging: EVs can completely reimagine the way we store energy
You can also check out all previous Year 2049 editions to learn about other impactful innovations shaping our future across all aspects of life.
How would you rate this week's edition?
Boring | Okay | Great
(Reply and let me know)








> all without requiring any additional steps or devices during authentication.
This is empirically false. What if you don't have a mobile device? The US Veterans Affairs login system used email/password. Someone decided that wasn't secure enough so they built a system which required a mobile device. With the new system there is no option to login if you don't have a smart phone. It lasted about a week before they allowed us to login with the old email/password system again. There are enough people who don't know how to use authentication apps or who refuse to get a mobile gadget for this to work as well as they think. I'm glad someone is thinking about the problems of passwords but they need someone on their team that isn't a 20-year-old living in San Francisco.
I would be in favor of dumping passwords altogether if a better system was available. Thankfully Apple remembers all of mine. I couldn’t. I know, they could potentially get hacked but what are you going to do? No one can remember hundreds of passwords.